路由¶
将请求连接到服务
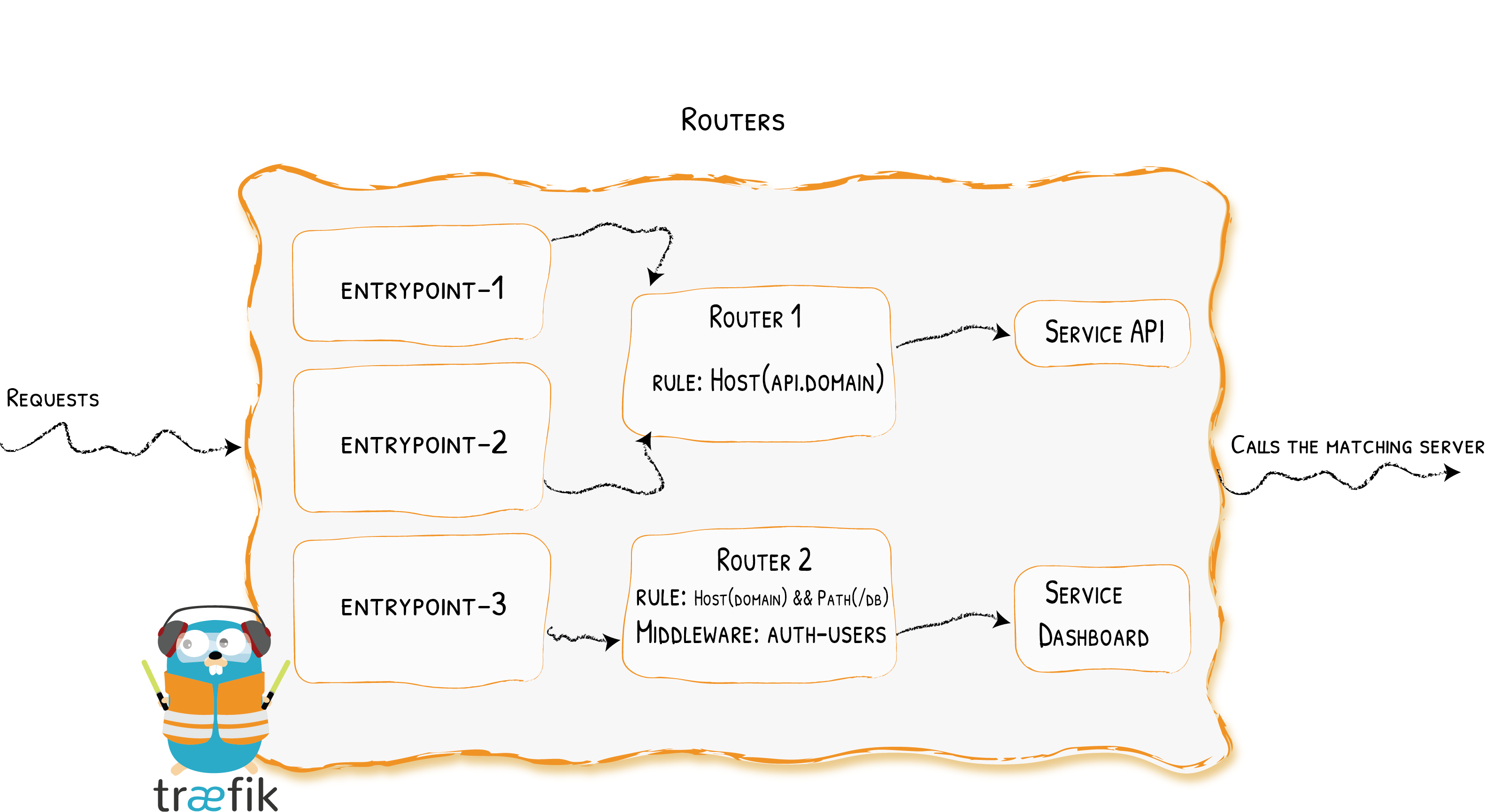
路由器负责将传入请求连接到可以处理它们的服务。在此过程中,路由器可以使用多个中间件 来更新请求,或者在将请求转发给服务之前采取行动。
配置示例¶
请求/ foo 由 service-foo 处理 - 使用文件提供程序
[http.routers]
[http.routers.my-router]
rule = "Path(`/foo`)"
service = "service-foo" http:
routers:
my-router:
rule: "Path(`/foo`)"
service: service-foo使用中间件 - 使用文件提供程序
[http.routers]
[http.routers.my-router]
rule = "Path(`/foo`)"
# declared elsewhere
middlewares = ["authentication"]
service = "service-foo" http:
routers:
my-router:
rule: "Path(`/foo`)"
# declared elsewhere
middlewares:
- authentication
service: service-foo将端口 3306 上的所有(非 tls)请求转发到数据库服务
## Static configuration ##
[entryPoints]
[entryPoints.web]
address = ":80"
[entryPoints.mysql-default]
address = ":3306"
## Dynamic configuration ##
[tcp]
[tcp.routers]
[tcp.routers.to-database]
entryPoints = ["mysql-default"]
# Catch every request (only available rule for non-tls routers. See below.)
rule = "HostSNI(`*`)"
service = "database"## Static configuration ##
entryPoints:
web:
address: ":80"
mysql-default:
address: ":3306"
## Dynamic configuration ##
tcp:
routers:
to-database:
entryPoints:
- "mysql-default"
# Catch every request (only available rule for non-tls routers. See below.)
rule: "HostSNI(`*`)"
service: database配置HTTP路由器¶
入口点¶
如果未指定,HTTP路由器将接受来自所有已定义入口点的请求。
如果要将路由器范围限制为一组入口点,请设置该entryPoints选项。
Listens to Every EntryPoint
## Static configuration ##
[entryPoints]
[entryPoints.web]
# ...
[entryPoints.web-secure]
# ...
[entryPoints.other]
# ...
## Dynamic configuration ##
[http.routers]
[http.routers.Router-1]
# By default, routers listen to every entry points
rule = "Host(`traefik.io`)"
service = "service-1"## Static configuration ##
entryPoints:
web:
# ...
web-secure:
# ...
other:
# ...
## Dynamic configuration ##
http:
routers:
Router-1:
# By default, routers listen to every entry points
rule: "Host(`traefik.io`)"
service: "service-1"Listens to Specific EntryPoints
## Static configuration ##
[entryPoints]
[entryPoints.web]
# ...
[entryPoints.web-secure]
# ...
[entryPoints.other]
# ...
## Dynamic configuration ##
[http.routers]
[http.routers.Router-1]
# won't listen to entry point web
entryPoints = ["web-secure", "other"]
rule = "Host(`traefik.io`)"
service = "service-1"## Static configuration ##
entryPoints:
web:
# ...
web-secure:
# ...
other:
# ...
## Dynamic configuration ##
http:
routers:
Router-1:
# won't listen to entry point web
entryPoints:
- "web-secure"
- "other"
rule: "Host(`traefik.io`)"
service: "service-1"Rule¶
规则是一组匹配器,用于确定特定请求是否符合特定条件。 如果验证为真,则路由器变为活动状态,调用中间件,然后将请求转发给服务。
Host is traefik.io
rule = "Host(`traefik.io`)"Host is traefik.io OR Host is containo.us AND path is /traefik
rule = "Host(`traefik.io`) || (Host(`containo.us`) && Path(`/traefik`))"下表列出了所有可用的匹配器:
| Rule | Description |
|---|---|
Headers(`key`, `value`) |
检查 key 标头中是否定义了一个带有值的密钥 value |
HeadersRegexp(`key`, `regexp`) |
检查 key 标头中是否定义了一个键,其值与正则表达式匹配 regexp |
Host(`domain-1`, ...) |
检查请求域是否针对给定的一个 domains。. |
HostRegexp(`traefik.io`, `{subdomain:[a-z]+}.traefik.io`, ...) |
检查请求域是否与给定域匹配 regexp。. |
Method(`GET`, ...) |
检查请求方法是给定的一个 methods(GET,POST,PUT,DELETE,PATCH) |
Path(`path`, `/articles/{category}/{id:[0-9]+}`, ...) |
匹配确切的请求路径。它接受一系列文字和正则表达式路径。 |
PathPrefix(`/products/`, `/articles/{category}/{id:[0-9]+}`) |
匹配请求前缀路径。它接受一系列文字和正则表达式前缀路径。 |
Query(`foo=bar`, `bar=baz`) |
Match`查询字符串参数。它接受一系列 key = value 对。 |
Regexp 语法
为了使用带有Host和Path表达式的正则表达式,必须声明一个任意命名的变量,后跟冒号分隔的正则表达式,全部用大括号括起来。 可以使用Go的regexp包支持的任何模式(例如:)/posts/{id:[0-9]+}。
使用运算符和括号组合匹配器
您可以使用AND(&&)和OR(||)运算符组合多个匹配器。您也可以使用括号。
规则,中间件和服务
该规则在“之前”任何中间件有机会工作之前进行评估,并且在“之前”将请求转发给服务。
Path Vs PathPrefix
使用Path,如果你的服务只的确切路径上侦听。例如,Path: /products匹配/products但不匹配/products/shoes
如果您的服务侦听特定的基本路径,但也在子路径上提供请求,请使用匹配器*Prefix*。
例如,PathPrefix: /products 匹配 /products也匹配/products/shoes和/products/shirts。
由于路径按原样转发,因此您的服务应该监听/products。
中间件¶
您可以将中间件 列表附加到每个HTTP路由器。 只有规则匹配,并且在将请求转发给服务之前,中间件才会生效。
服务¶
您必须为每个路由器附加服务。 服务是路由器的目标。
仅限HTTP
HTTP路由器只能定位HTTP服务(而不是TCP服务)。
TLS¶
General¶
Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services). 当指定TLS部分时,它指示Traefik当前路由器仅专用于HTTPS请求(并且路由器应忽略HTTP(非TLS)请求)。 Traefik将终止SSL连接(意味着它将解密数据发送到服务)。
配置路由器仅接受HTTPS请求
[http.routers]
[http.routers.Router-1]
rule = "Host(`foo-domain`) && Path(`/foo-path/`)"
service = "service-id"
# will terminate the TLS request
[http.routers.Router-1.tls]http:
routers:
Router-1:
rule: "Host(`foo-domain`) && Path(`/foo-path/`)"
service: service-id
# will terminate the TLS request
tls: {}HTTPS和ACME
在当前版本中,启用ACME 后,自动证书生成将应用于声明TLS部分的每个路由器。
HTTP和HTTPS路由
如果需要为HTTP和HTTPS请求定义相同的路由,则需要定义两个不同的路由器:一个带有tls部分,一个没有。
HTTP和HTTPS路由
[http.routers]
[http.routers.my-https-router]
rule = "Host(`foo-domain`) && Path(`/foo-path/`)"
service = "service-id"
# will terminate the TLS request
[http.routers.my-https-router.tls]
[http.routers.my-http-router]
rule = "Host(`foo-domain`) && Path(`/foo-path/`)"
service = "service-id"http:
routers:
my-https-router:
rule: "Host(`foo-domain`) && Path(`/foo-path/`)"
service: service-id
# will terminate the TLS request
tls: {}
my-http-router:
rule: "Host(`foo-domain`) && Path(`/foo-path/`)"
service: service-idoptions¶
options字段可以对TLS参数进行细粒度控制。
它指的是TLS选项,仅在Host定义规则时才会应用。
服务器名称关联
即使有人可能会得到TLS选项引用映射到路由器或路由器的规则, 但应该意识到它实际上只映射到Host规则部分中找到的主机名。 当然,规则中也可能有几个Host部分,在这种情况下,TLS选项引用将映射到尽可能多的主机名.
要记住的另一件事是:从上面提到的映射中选择TLS选项,并根据TLS握手期间提供的服务器名称,这一切都发生在路由实际发生之前。
配置TLS选项
[http.routers]
[http.routers.Router-1]
rule = "Host(`foo-domain`) && Path(`/foo-path/`)"
service = "service-id"
# will terminate the TLS request
[http.routers.Router-1.tls]
options = "foo"
[tls.options]
[tls.options.foo]
minVersion = "VersionTLS12"
cipherSuites = [
"TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256",
"TLS_RSA_WITH_AES_256_GCM_SHA384"
]http:
routers:
Router-1:
rule: "Host(`foo-domain`) && Path(`/foo-path/`)"
service: service-id
# will terminate the TLS request
tls:
options: foo
tls:
options:
foo:
minVersion: VersionTLS12
cipherSuites:
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_RSA_WITH_AES_256_GCM_SHA384冲突的TLS选项
由于TLS选项引用映射到主机名,因此如果配置引入了相同主机名(来自Host规则)与两个TLS选项引用匹配的情况,则会发生冲突,例如下面的示例:
[http.routers]
[http.routers.routerfoo]
rule = "Host(`snitest.com`) && Path(`/foo`)"
[http.routers.routerfoo.tls]
options = "foo"
[http.routers]
[http.routers.routerbar]
rule = "Host(`snitest.com`) && Path(`/bar`)"
[http.routers.routerbar.tls]
options = "bar"http:
routers:
routerfoo:
rule: "Host(`snitest.com`) && Path(`/foo`)"
tls:
options: foo
routerbar:
rule: "Host(`snitest.com`) && Path(`/bar`)"
tls:
options: bar如果发生这种情况,两个映射都将被丢弃,并且snitest.com这些路由器的主机名(在本例中)将与默认的TLS选项相关联。
certResolver¶
如果 certResolver 已定义,Traefik将尝试根据路由器Host和HostSNI规则生成证书。
[http.routers]
[http.routers.routerfoo]
rule = "Host(`snitest.com`) && Path(`/foo`)"
[http.routers.routerfoo.tls]
certResolver = "foo"http:
routers:
routerfoo:
rule: "Host(`snitest.com`) && Path(`/foo`)"
tls:
certResolver: foo规则中的多个主机
该规则Host(test1.traefik.io,test2.traefik.io) 将请求具有主域test1.traefik.io和SAN 的证书test2.traefik.io。
domains¶
您可以为每个主域设置SAN(备用域)。 每个域必须有指向Traefik的A / AAAA记录。 每个域和SAN都将导致证书请求。
[http.routers]
[http.routers.routerbar]
rule = "Host(`snitest.com`) && Path(`/bar`)"
[http.routers.routerbar.tls]
certResolver = "bar"
[[http.routers.routerbar.tls.domains]]
main = "snitest.com"
sans = "*.snitest.com"http:
routers:
routerbar:
rule: "Host(`snitest.com`) && Path(`/bar`)"
tls:
certResolver: "bar"
domains:
- main: "snitest.com"
sans: "*.snitest.com"ACME v2支持通配符证书。 正如Let's Encrypt的帖子所述,通配符证书只能通过DNS-01生成。
很可能根域也应该收到证书,因此需要将其指定为SAN并DNS-01执行2个配置。 在这种情况下,两个域生成的DNS TXT记录是相同的。尽管此行为符合DNS RFC,但它可能会导致问题,因为所有DNS提供程序都会将DNS记录缓存一段时间(TTL),并且此TTL可能大于挑战超时,从而导致DNS-01质询失败。
Traefik ACME客户端库LEGO支持部分但不是所有DNS提供商来解决此问题。 的支持的provider表指示是否它们允许通配符域及其根域产生证书
Note
通配符证书只能通过DNS-01 challenge.进行验证。
Double Wildcard Certificates
无法为域请求双通配符证书(例如..local.com)。
配置TCP路由器¶
General¶
如果HTTP路由器和TCP路由器都侦听相同的入口点,则TCP路由器将在 HTTP路由器之前应用。 如果没有找到TCP路由器的匹配路由,则HTTP路由器将接管。
入口点¶
如果未指定,TCP路由器将接受来自所有已定义入口点的请求。 如果要将路由器范围限制为一组入口点,请设置入口点选项。
Listens to Every Entry Point
## Static configuration ##
[entryPoints]
[entryPoints.web]
# ...
[entryPoints.web-secure]
# ...
[entryPoints.other]
# ...
## Dynamic configuration ##
[tcp.routers]
[tcp.routers.Router-1]
# By default, routers listen to every entrypoints
rule = "HostSNI(`traefik.io`)"
service = "service-1"
# will route TLS requests (and ignore non tls requests)
[tcp.routers.Router-1.tls]## Static configuration ##
entryPoints:
web:
# ...
web-secure:
# ...
other:
# ...
## Dynamic configuration ##
tcp:
routers:
Router-1:
# By default, routers listen to every entrypoints
rule: "HostSNI(`traefik.io`)"
service: "service-1"
# will route TLS requests (and ignore non tls requests)
tls: {}Listens to Specific Entry Points
## Static configuration ##
[entryPoints]
[entryPoints.web]
# ...
[entryPoints.web-secure]
# ...
[entryPoints.other]
# ...
## Dynamic configuration ##
[tcp.routers]
[tcp.routers.Router-1]
# won't listen to entry point web
entryPoints = ["web-secure", "other"]
rule = "HostSNI(`traefik.io`)"
service = "service-1"
# will route TLS requests (and ignore non tls requests)
[tcp.routers.Router-1.tls]
```
```yaml tab="YAML"
## Static configuration ##
entryPoints:
web:
# ...
web-secure:
# ...
other:
# ...
## Dynamic configuration ##
tcp:
routers:
Router-1:
# won't listen to entry point web
entryPoints:
- "web-secure"
- "other"
rule: "HostSNI(`traefik.io`)"
service: "service-1"
# will route TLS requests (and ignore non tls requests)
tls: {}
```
### Rule
| Rule | Description |
|--------------------------------|-------------------------------------------------------------------------|
| ```HostSNI(`domain-1`, ...)``` | Check if the Server Name Indication corresponds to the given `domains`. |
!!! important "HostSNI & TLS"
It is important to note that the Server Name Indication is an extension of the TLS protocol.
Hence, only TLS routers will be able to specify a domain name with that rule.
However, non-TLS routers will have to explicitly use that rule with `*` (every domain) to state that every non-TLS request will be handled by the router.
### Services
You must attach a TCP [service](../services/index.md) per TCP router.
Services are the target for the router.
!!! note "TCP Only"
TCP routers can only target TCP services (not HTTP services).
### TLS
#### General
When a TLS section is specified, it instructs Traefik that the current router is dedicated to TLS requests only (and that the router should ignore non-TLS requests).
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
By default, Traefik will terminate the SSL connections (meaning that it will send decrypted data to the services), but Traefik can be configured in order to let the requests pass through (keeping the data encrypted), and be forwarded to the service "as is".
??? example "Configuring TLS Termination"
```toml tab="TOML"
[tcp.routers]
[tcp.routers.Router-1]
rule = "HostSNI(`foo-domain`)"
service = "service-id"
# will terminate the TLS request by default
[tcp.routers.Router-1.tls]
```
```yaml tab="YAML"
tcp:
routers:
Router-1:
rule: "HostSNI(`foo-domain`)"
service: service-id
# will terminate the TLS request by default
tld: {}
```
??? example "Configuring passthrough"
```toml tab="TOML"
[tcp.routers]
[tcp.routers.Router-1]
rule = "HostSNI(`foo-domain`)"
service = "service-id"
[tcp.routers.Router-1.tls]
passthrough = true
```
```yaml tab="YAML"
tcp:
routers:
Router-1:
rule: "HostSNI(`foo-domain`)"
service: service-id
tls:
passthrough: true
```
!!! note "TLS & ACME"
In the current version, with [ACME](../../https/acme.md) enabled, automatic certificate generation will apply to every router declaring a TLS section.
#### `options`
The `options` field enables fine-grained control of the TLS parameters.
It refers to a [TLS Options](../../https/tls.md#tls-options) and will be applied only if a `HostSNI` rule is defined.
??? example "Configuring the tls options"
```toml tab="TOML"
[tcp.routers]
[tcp.routers.Router-1]
rule = "HostSNI(`foo-domain`)"
service = "service-id"
# will terminate the TLS request
[tcp.routers.Router-1.tls]
options = "foo"
[tls.options]
[tls.options.foo]
minVersion = "VersionTLS12"
cipherSuites = [
"TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256",
"TLS_RSA_WITH_AES_256_GCM_SHA384"
]
```
```yaml tab="YAML"
tcp:
routers:
Router-1:
rule: "HostSNI(`foo-domain`)"
service: service-id
# will terminate the TLS request
tls:
options: foo
tls:
options:
foo:
minVersion: VersionTLS12
cipherSuites:
- "TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256"
- "TLS_RSA_WITH_AES_256_GCM_SHA384"
```
#### `certResolver`
See [`certResolver` for HTTP router](./index.md#certresolver) for more information.
```toml tab="TOML"
[tcp.routers]
[tcp.routers.routerfoo]
rule = "HostSNI(`snitest.com`)"
[tcp.routers.routerfoo.tls]
certResolver = "foo"tcp:
routers:
routerfoo:
rule: "HostSNI(`snitest.com`)"
tls:
certResolver: foodomains¶
See domains for HTTP router for more information.
[tcp.routers]
[tcp.routers.routerbar]
rule = "HostSNI(`snitest.com`)"
[tcp.routers.routerbar.tls]
certResolver = "bar"
[[tcp.routers.routerbar.tls.domains]]
main = "snitest.com"
sans = "*.snitest.com"tcp:
routers:
routerbar:
rule: "HostSNI(`snitest.com`)"
tls:
certResolver: "bar"
domains:
- main: "snitest.com"
sans: "*.snitest.com"